Introduction
In the summer of this year I built my first ever PC, no its not the first PC I’ve owned, its the first one I’ve built from scratch. After having built it, I came across an odd error that took me sometime to troubleshoot and for which I couldn’t find a really straightforward explanation, so here is my post explaining the issues I encountered with with Disk Encryption on Windows 10 Home.
Bitlocker is not Available
Bitlocker is not available on Windows 10 Home.
I didn’t know this, I was surprised and disappointed and as a cyber security specialist I was disappointed that I could not do any native OS drive encryption. Then I found that there was an alternative called, unremarkably, “Device Encryption”. If it is available to you, it can be found in Settings > Update & Security – I say if it is available to you because it is hardware dependant and it seems that a lot of hardware, even fairly new hardware, doesn’t support all of the requirements.
Here is a screenshot from a system that is compatible
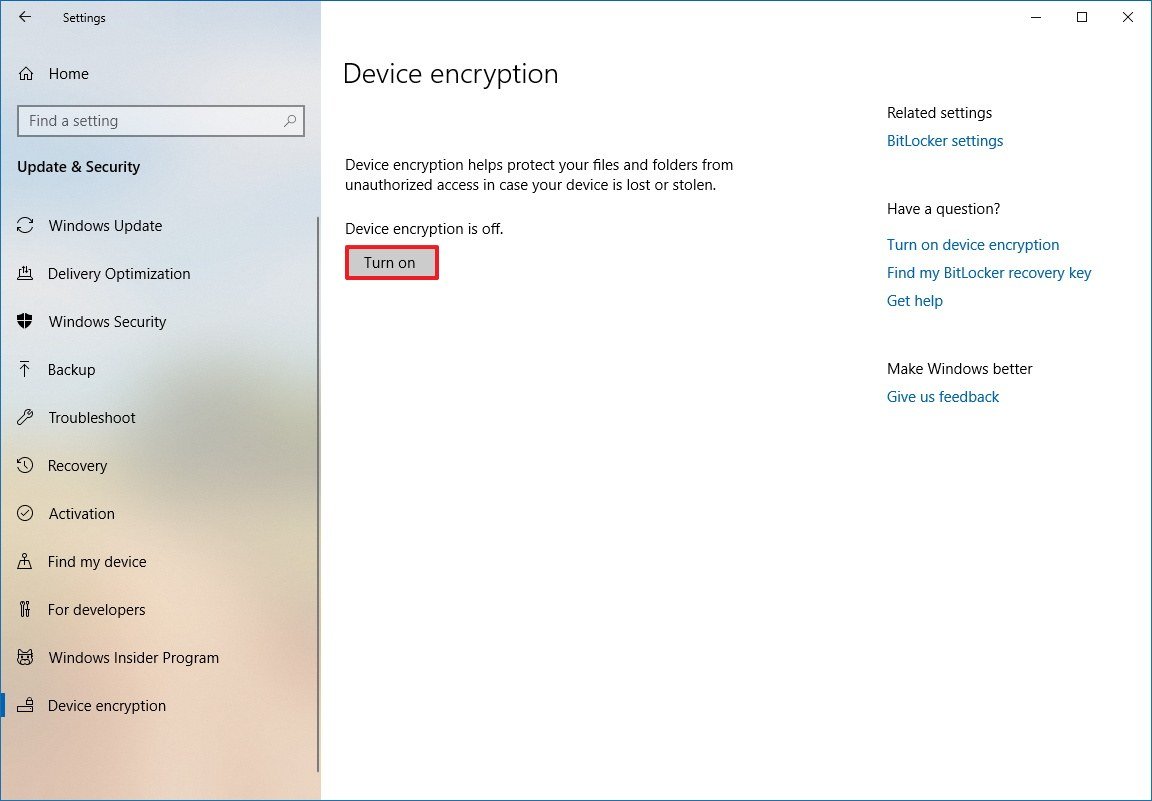
If Device Encryption does not appear on that page, it likely means that your hardware is not compatible in its current state. You can check this easily by using the System Information app that Microsoft kindly include.
Go to Search type System Information and click on Run as Administrator
In the window that opens at the very bottom of the screen you will see an entry for Device Encryption Support, change the column widths so you can read the entire message.
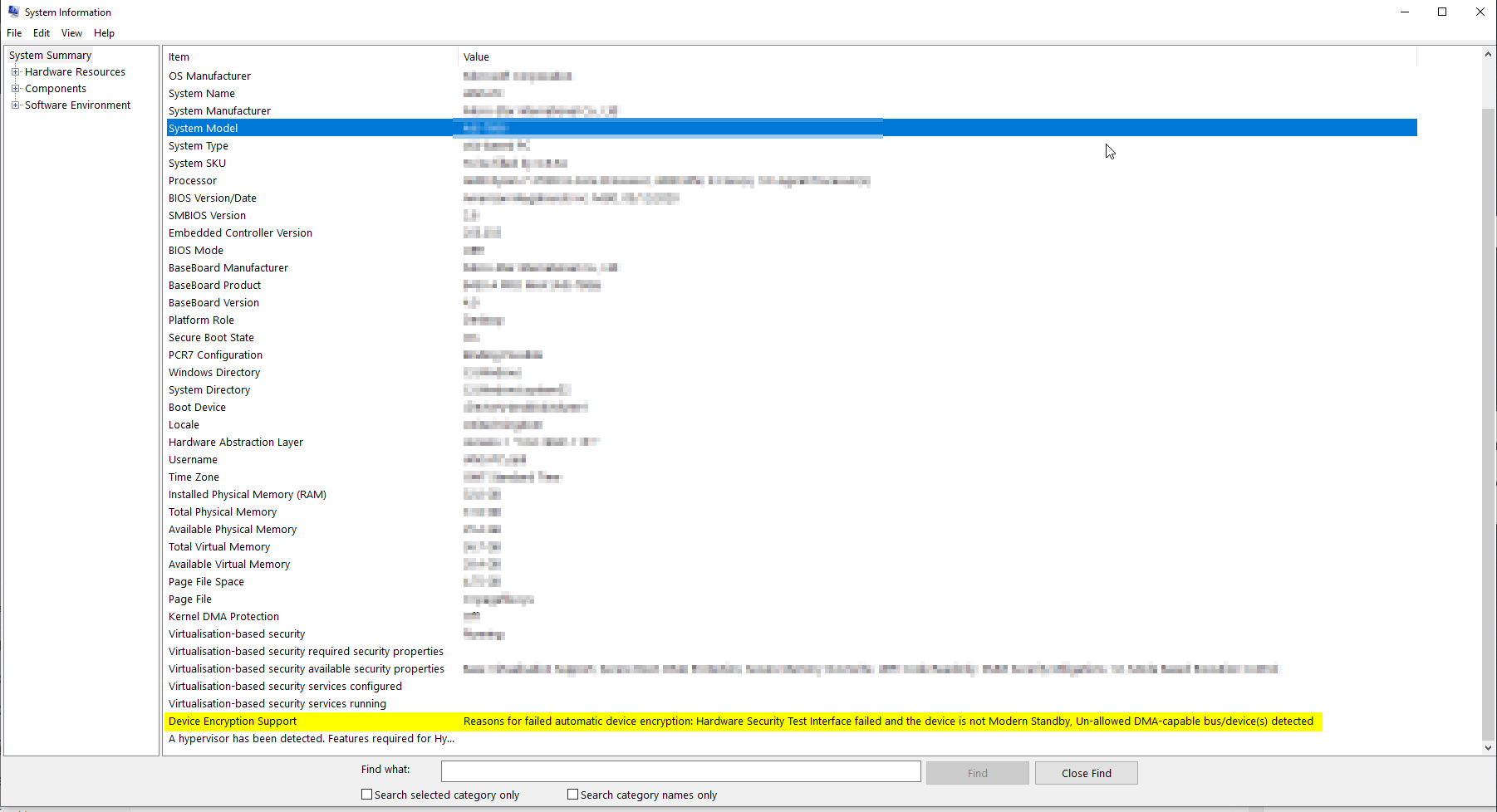
If you could read the image above you would see that the entry on my PC said:
Device Encryption Support: Reasons for failed automatic device encryption: PCR7 binding is not supported, Hardware Security Test Interface failed and the device is not Modern Standby, Un-allowed DMA-capable bus/device(s) detected
This is a list of at least three different errors
- PCR7 binding is not supported
- There are Un-allowed DMA capable devices
- The device does not support Modern Standby
Lets look at each of these in turn
PCR7 Binding is not supported
This refers to secure boot, it’s that simple.
You can check if you have secure boot available in your BIOS you also need to check that secure boot is using UEFI. I cannot tell you how to do this as every BIOS is different, but you can check for secure boot through PowerShell.
To check in PowerShell open the search menu, type PowerShell and open the PowerShell application as administrator.
In the shell windows that opens type Confirm-SecureBootUEFI
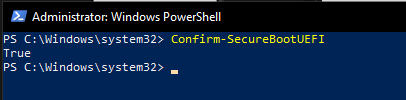
In this example I had already enabled it and you can see that the command returned True, so Secure boot is enabled. Its likely, if you are reading this and you have the PCR7 Binding error that yours will return False
I can’t tell you how to do that as each BIOS will be different depending on manufacturer. I had to enable UEFI and disable CSR. Once I had managed to enable this windows reported that secure boot was enabled it enabled in Settings > Windows Security > Device Security

Once I’d done this the PCR7 Binding error disappeared from System Info
Un-Allowed DMA Capable Devices
I am going to tell you what this means and how to workaround it. I do so with a warning that there are issues doing so and you reduce the security of your system potentially opening it to DMA attacks. A lot of DMA attacks have been mitigated ion later versions of windows but if you make these changes then you do so at your own risk.
You can read about DMA attacks on Wikipedia
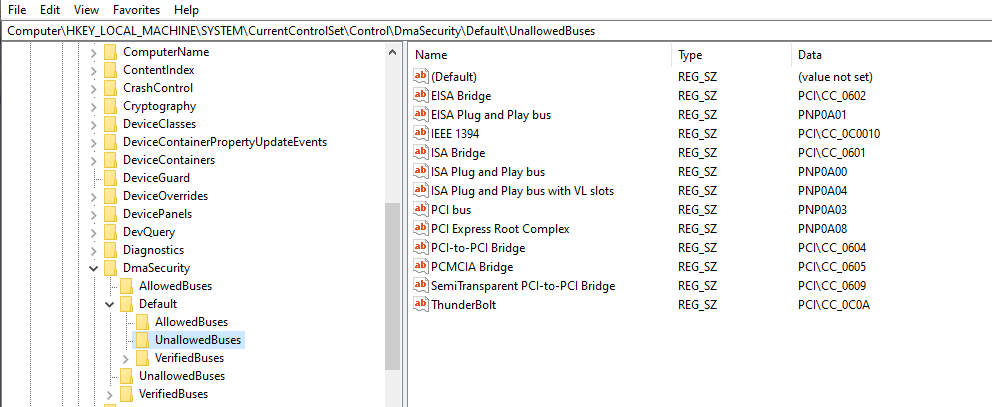
Windows lists Allowed, UnAllowed and Verified DMA devcies in the registry with their PCI ID, you can see them at:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DmaSecurity
Mine were all under the default key
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\DmaSecurity\Default
You can view them by using Regedit or PowerShell
Regedit
Open the search menu, type Regedit and click on the Regedit application
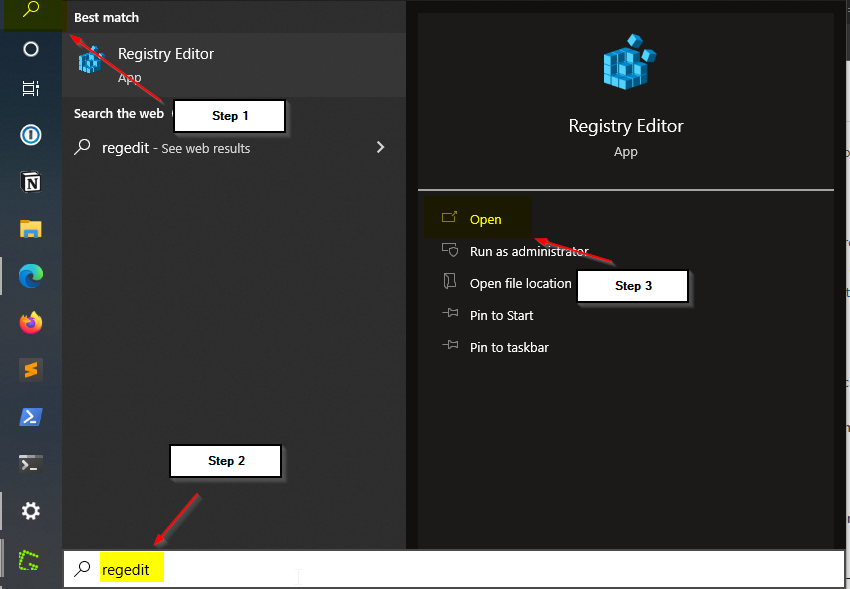
Navigate to the appropriate Hive and Key and inspect the listings
PowerShell
To view the keys and values in PowerShell open the search menu, type PowerShell and open the PowerShell application
In the shell window that opens type the following commands, make sure you include the space and full stop after Get-Item
Set-Location HKLM:\system\currentcontrolset\control\dmasecurity\default\UnallowedBuses Get-Item . #make sure you add the space and a full stop
This will show you all the entries in the UnallowedBuses registry key with their name and value
Fixing the Error
To remove the DMA error you need to remove these entries or move them to AllowedBuses. To do that you need to take ownership of the UnallowedBuses and AllowedBuses Key and then give yourself full access to both keys. There is an MS article that references this process for Bitlocker, it is the same process for Device Encryption. You can read that article on the MS Docs site – Un-allowed DMA capable bus/device(s) detected
Remember the earlier warning, this may be opening the potential for DMA attacks. I suggest you check with the manufacturer of the device if they can provide any information on the component’s use of DMA and the safety of doing this.
Some articles suggested working through them one at a time to find the ones that were causing the issue, but I had to remove them all from UnallowedBuses.
Modern Standby
This one relates to Power Settings and the capabilities of your motherboard to support a different standard when it is asleep or in standby . It is discussed in this MS Docs article – What is Modern Standby
Your motherboard must be capable of supporting Standby (S0). You can identify if this is supported by opening a command prompt and typing a simple command. to open the command prompt open the search menu, type cmd and click to open the appliaction.
One open type powercfg /a and press enter
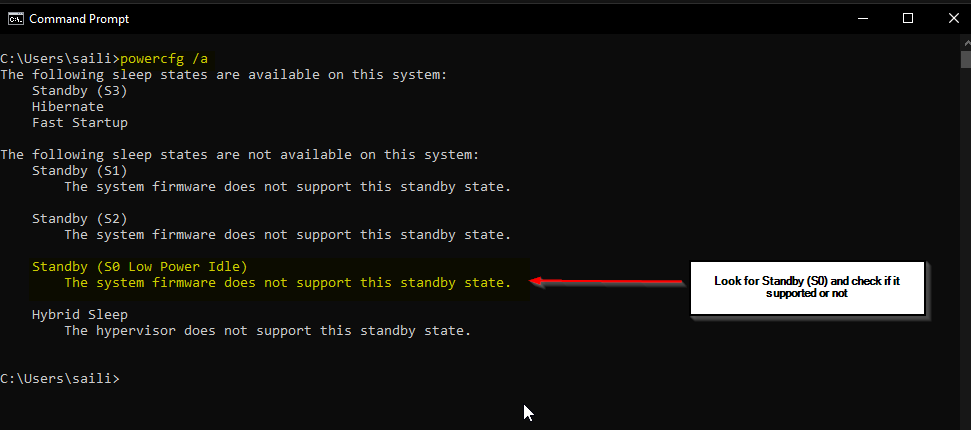
In my case it appears that it is not supported and that is the end of that, I cannot take advantage of Device Encryption without a firmware upgrade or a new motherboard. I’ve written to the manufacturers to see if there are plans to support it or if I have missed a setting somewhere in the BIOS that would enable it. I’ll update this post if they respond.
Conclusion
In my opinion, Device Encryption shouldn’t be this difficult to implement for home users and the error messaging could be much better, even provided in the Device Security Settings page rather than in system info. In this day and age encryption at rest should be the default.
Despite this I hope that this article will help guide you and maybe you can get yours to work, or at least not spend hours trying to decipher the error messaging through multiple Google searches and Microsoft Answers to find that it will not.